CryptIt
CryptIt
Rating
 Downloads
: 218
Downloads
: 218
|
Price : 8
Shareware
Size :
0.04MB |
|
|
Version : 1.4 |
Minor Update
|
| OS
Windows2000 , WinXP , Windows2003 , Windows Vista Starter , Windows Vista Home Basic , Windows Vista Home Premium , Windows Vista Business , Windows Vista Enterprise , Windows Vista Ultimate , Windows Vista Home Basic x64 , Windows Vista Home Premium x64 , Windows Vista Business x64 , Windows Vista Enterprise x64 , Windows Vista Ultimate x64
|
|
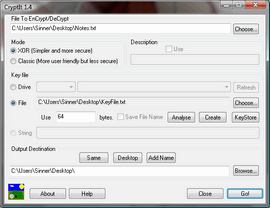
Assembly Language XOR File encrypter
Many file encryptors use strategies that rely on the theory of computational security, that is the difficulty of key factorisation prevents decryption ofthe file. Yet this method may not really work forever. It utilized to be considered that a 56 bit key was unbreakable to brute force attacks, but the government from the USA now needs all Top Secret information to use keys of at least 192 bits. This bar will keep raising as computing power increases. (It is asserted by some though that will this can never happen owing to the laws of physics! ) This program is designed to use conventional XOR encryption on keys that are the same size as the particular file to become encrypted. Moreover, if you use a good unpredictable file that is the same size (or larger) than the original file and you use this document only once, this is usually called an one-time pad and it is completely unbreakable, even to computers 1000 years from now. This is usually because there is simply no algorithm at all, simply a big key, and thus there is no pattern to follow once you have decrypted any area of the file. Thus attempts in order to decrypt it could end result in any file, plus there would be no chance to verify that it has decrypted correctly. This program can also has some convenience features for example being capable to automatically use cushion files generated by the program GigAlarm, generate key files (from a stream cipher and thus not perfect for OTP usage) plus also analyse the appropriateness of your chosen essential file.
This program also has an ability to use removable media (USB drives, CDs, floppies) as a key code book, further increasing the security and convenience associated with the method. In case your requirements are more simpler then you can certainly also use a word (string), but the advantages of the XOR method are lost then. Explanations can be stored inside the encrypted file, as nicely as the file name of the code. Order line operation is furthermore supported and This program is usually written in Assembly Language for maximum efficiency.
|
|
|
|
|
Questions or Problems with This Program ! |
Report Bad Link |
|
If you have any questions please post it and we will answer it asap .
[ Comments allowed for anonymous users, please dont register ]
|
So far so good :
No Comments :: No Problems :: No Answers
|
| |
Other software for same Developer :
|
Please Scan for Viruses before use .

 Downloads
: 218
Downloads
: 218