Whitenoise Computer File Security
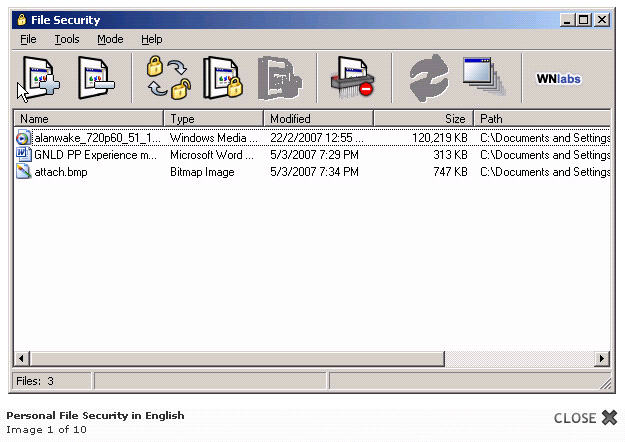
Whitenoise Computer File Security
Rating
 By 3 Users
Downloads
: 7
By 3 Users
Downloads
: 7
|
Price : 19.99
Demo
Size :
7.34MB |
|
|
Version : 5.0 |
Major Update
|
| OS
Windows2000 , WinXP , Windows2003
|
|
Whitenoise International Export Permitted CSE
SCM How did Wiki Water leaks happen! A disgruntled staff with an agenda moves to work together with USB display drives and copies constrained files from the server, since there is NO enough secure network. Preventing typically the Wiki Leaks scenario in addition to creating a secure community requires ONLY three items:
1 ) Secure network accessibility. All users logging on the network are determined by a special key of which performs dynamic identity confirmation and authentication (DIVA). a couple of. Secure data transmission. Just about all data transmission occurs inside an encrypted state. Protected File Interchange 2 (SFI) establishes a dynamic allocated key infrastructure (DDKI) construction. 3. Secure data safe-keeping. All data is immediately uniquely encrypted using a major related to the user’s name and password, in addition to saved in a “virtual container” SPECIFIC to of which user in a encrypted express. Whitenoise ensures 100% community security inside the SIMPLEST method to install, learn in addition to use. Data is obviously safeguarded with UNIQUE identity centered encryption so it is usually ALWAYS secure in transmitting and storage. At virtually any point when there is usually an unauthorized attempt to be able to access files or capabilities, the INHERENT INTRUSION DIAGNOSIS instantly recognizes that GORGEOUS WOMAN is not in synch and the network self-protects by the AUTOMATIC WITHDRAWAL, REVERSAL, OVERTURNING, ANNULMENT of network access to be able to that key. Whitenoise’s remedy is scalable, interoperable in addition to works with ANY sort of network. The a few applications needed to protected a network can end up being incorporated into ONE management gaming console. Creating employees’ computers in addition to determining which files/folders/applications they will can see and obtain is EASILY made by typically the system administrator through typically the normal Windows operating method interface. Learning and executing COMPLETE system administration in addition to COMPLETE secure network installation and distribution of take some time takes approximately two several hours. Secure single-sign on community access and login is usually SIMPLE and requires LITTLE training of employees. Typically the system administrator can constantly recover data.
|
|
|
|
|
Questions or Problems with This Program ! |
Report Bad Link |
|
If you have any questions please post it and we will answer it asap .
[ Comments allowed for anonymous users, please dont register ]
|
So far so good :
No Comments :: No Problems :: No Answers
|
| |
Please Scan for Viruses before use .

 By 3 Users
Downloads
: 7
By 3 Users
Downloads
: 7