| It features on-the-fly AES encryption, by creating virtual encrypted disk drives, where you can hide files and folders, keep them encrypted at all times, but still work with them just like you work with normal files. It is going to protect your confidential | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 268 |
| Version | 1.8 |
| Date | 09/06/2010 |
| License | Shareware |
| Note that web publishers of secure SWF documents might have implemented DRM regulates to prevent copying, stop publishing, stop decompiling, and run out happy to protect copyright plus prevent intellectual property robbery. Copy control steps enforce | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 267 |
| Version | 1.1.8 |
| Date | 09/11/2009 |
| License | Freeware |
| CryptoExpert uses a real-time moving encryption system to encrypt and decrypt data. Your own files are stored within the encrypted form upon virtual hard disk with security password authentication, nevertheless it is usually requested by any program, | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 263 |
| Version | 7.9.4 |
| Date | 06/06/2009 |
| License | Shareware |
| This program is a fantastically simple way to connect to MySQL using SSH encrypted tunnels. The program features a visual interface, that clearly shows you which connections using the SSH tunnel and which are not. | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 256 |
| Version | 1.1.0.0 |
| Date | 18/08/2007 |
| License | Shareware |
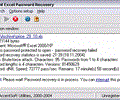
| To reduce time of searching for the password to a workbook, the program has 3 search methods: a brute-force attack, an attack simply by an enhanced mask, a good enhanced dictionary-based attack. The built-in Task Creation Wizard will guide an inexperienced | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 256 |
| Version | 2.90 |
| Date | 25/03/2009 |
| License | Shareware |
| PhoneCrypt is a telephone encryption software designed to combat eavesdropping and interception by providing Military Grade security for your confidential mobile phone conversations. Effectively eliminating the chance of a 3rd party eavesdropping | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 256 |
| Version | 1.4 |
| Date | 27/10/2006 |
| License | Shareware |
| The IDEA motorist is installed simply good enough - you should place the particular driver's distributive in certain directory, then run BestCrypt Service Manager from the BestCrypt Program Group and use the "Add.. The IDEA driver distributive contains | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 256 |
| Version | 7.20 |
| Date | 17/07/2005 |
| License | Freeware |
| The objective of the software is to offer you royalty-free access to encryption/decryption mechanisms to make your work more secure and easy to transfer. With this particular software, you can encrypt a single file or a complete folder with almost | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 255 |
| Version | 0.1 |
| Date | 08/12/2005 |
| License | Freeware |
| File Own Guard designed with regard to strong file encryption with multi-choice compression on the fly by a range of crypto-algorithms (AES, MARS, RC6, SERPENT, TWOFISH), secure file removal (shredding) using one of the eight special algorithm (DoD, | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 253 |
| Version | 2.1 |
| Date | 15/11/2007 |
| License | Shareware |
| Certificate encrypted documents cannot be exceeded on to a third person – thus making them the ideal solution with regard to eBook distribution or safe sealing of documents. These encrypted files can only be decrypted in case the recipient has in | |
Rating
|
|
 Rate This Program |
Rate This Program |
 Report error
Report error |
|
| Hits | 252 |
| Version | 5.0.2 |
| Date | 21/12/2010 |
| License | Commercial |